Cloud computing and analysis features of cloud information security
The current state of application and development of cloud computing, the main advantages and disadvantages of their use in the states, enterprises and in scientific activity. Guidance documents in the field of cloud computing information security.
| Рубрика | Программирование, компьютеры и кибернетика |
| Вид | статья |
| Язык | английский |
| Дата добавления | 23.10.2020 |
| Размер файла | 94,3 K |
Отправить свою хорошую работу в базу знаний просто. Используйте форму, расположенную ниже
Студенты, аспиранты, молодые ученые, использующие базу знаний в своей учебе и работе, будут вам очень благодарны.
Размещено на http://www.allbest.ru/
CLOUD COMPUTING AND ANALYSIS FEATURES OF CLOUD INFORMATION SECURITY
Andrushchak LYe, Martsenyuk V.P.,
Androshchuk I.V,
Chudovets V.V., Poteychuk M.I.
Анотація
Андрущак І.Є., Марценюк В.П., Андрощук І.В., Чудовець В.В., Потейчук М.1' Хмарні обчислення та аналіз особливостей інформаційної безпеки в хмарі. У статті розглядається сучасний стан застосування та розвитку хмарних обчислень, основні переваги та недоліки їх використання в державах, на підприємствах і в науковій діяльності. Визначаються і аналізуються стандарти, нормативні та керівні документи в галузі інформаційної безпеки хмарних обчислень, розроблені Cloud Security Alliance (CSA), Європейським агентством мережевої та інформаційної безпеки (ENISA) і Національним інститутом стандартів і технологій (NIST), а також наводяться результати детального аналізу питань інформаційної безпеки в хмарі.
Ключові слова: хмарні обчислення, інформаційна безпека, порівняльний аналіз, недоліки та переваги обчислень в хмарах.
Аннотация
Андрущак И.Е., Марценюк В.П., Андрощук И.В., Чудовець В.В., Потейчук М.І.' Облачные вычисления и анализ особенностей информационной безопасности в облаке. В статье рассматривается современное состояние применения и развития облачных вычислений, основные преимущества и недостатки их использования в государствах, на предприятиях и в научной деятельности. Определяются и анализируются стандарты, нормативные и руководящие документы в области информационной безопасности облачных вычислений, разработанные Cloud Security Alliance (CSA), Европейским агентством сетевой и информационной безопасности (ENISA) и Национальным институтом стандартов и технологий (NIST), а также приводятся результаты детального анализа вопросов информационной безопасности в облаке.
Ключевые слова: облачные вычисления, информационная безопасность, сравнительный анализ, недостатки и преимущества вычислений в облаках.
Annotation
cloud computing information security
Andrushchak LYe, Martsenyuk V.P., Androshchuk I.V, Chudovets V.V.,Poteychuk M.I. Cloud computing and analysis features of cloud information security. The article discusses the current state of application and development of cloud computing, the main advantages and disadvantages of their use in the states, enterprises and in scientific activity. The standards, regulations and guidance documents in the field of cloud computing information security are developed and analyzed, developed by the Cloud Security Alliance (CSA), the European Network and Information Security Agency (ENISA) and the National Institute of Standards and Technology (NIST), and the results of a detailed analysis of the issues information security in the cloud.
Keywords: cloud computing, information security, benchmarking, disadvantages and benefits of cloud computing.
Formulation of the problem
The rapid development of broadband Internet has become one of the impetus for the emergence of cloud services as an IT outsourcing tool. Today, the Internet is widely used in many industries. Given the rapid growth of the IT industry and the number of services it can provide, the use of IT technologies for business development is right strategically. Modern business uses technological developments not only to automate business processes, but also to translate new ideas and ways to gain competitive advantage. Becoming a leader in any business is not enough today. Having achieved the desired result, it is important for managers to be able to retain leadership both in an accurate and strategic perspective, based on a rational approach taking into account the development of the IT industry. With the rapid development of information technologies and the improvement of technical means, the management of companies raises the problem of how to promptly track the emergence of technological innovations and timely implement them in the social and technological processes of their activities.
Currently, no educational institution can operate effectively without the use of modern information technology. At the same time, the maintenance and development of each IT center's own IT infrastructure is very expensive. Institutions spend large sums on computer equipment, telecommunication equipment and software. Cloud computing is a good alternative to the classic training model. Its main advantage can be considered significant savings of the educational institution in which they are used. In this case, the computer infrastructure and / or information services are provided as "cloud" provider services. The only thing that cloud teachers need to offer to teachers and students is access to the Internet. The domestic cloud technology model is becoming one of the most important in the development of information technology outsourcing. Today, cloud technologies are being actively implemented in the day-to-day operations of organizations. This is facilitated by the current conditions of the market economy of Ukraine, where a culture of providing services and supporting complex information systems has already been created. Experience has shown that working for the cloud is practically an economical step for virtually all sectors of the consumer business. First of all, this applies to large corporations as well as to small and medium-sized enterprises, regardless of their field of activity. However, it is now doubtful whether cloud services are feasible for small companies because their computer resources are too low. The attractiveness of cloud products increases as the company's presence on the Internet increases. In the current reality, clouds are a new way of developing the IT industry. The vast majority of Ukrainian business participants are already using cloud services.
It is not easy to understand which cloud to apply to a particular business, but it is not too difficult. To begin with, we need to start with how the internal information component of an organization's activity is developed. If the company has its own developed IT infrastructure, it is not always logical to completely abandon the available resources and move to the cloud. If strict control requirements are required, and confidential information (eg financial sphere) is available, then hybrid clouds should be used here. It is recommended to use public clouds (e-commerce, analytics) to solve specific problems. If the business is tasked with improving the efficiency of the current IT infrastructure, then in this case it would be more advisable to introduce a private cloud, which will minimize the cost of its support, increase its flexibility and reduce the timeframe of IT projects [1].
Analysis of research
Cloud is a new business model for providing and receiving information services. This model promises to reduce operating and capital costs. It allows IT departments to focus on strategic projects rather than the routine tasks of managing their own data center.
There are many definitions of "cloud computing" to date. Most often they differ in their meaning and accents. Let's look at some of these definitions to understand what "cloud computing" is from different perspectives. Cloud computing is a dynamically weighted way to access external computing resources in the form of an Internet-based service, without the user having any particular knowledge of the cloud infrastructure or management skills of that cloud. technology. Cloud computing is software that is accessible to the user over the Internet or on a LAN as a service, allowing the use of a convenient interface for remote access to dedicated resources (computing resources, applications and data). The computer acts as an average terrestrial connected to the Network. Computers that perform cloud computing are called "cloud computing." In this case, the load between the computers included in the "cloud" is split automatically.
Cloud computing is not only a technological innovation in IT, but also a way to create new business when small IT vendors, including in the regions, have the opportunity to quickly market their services and few a costly way to embody your business ideas. Cloud computing, combined with investment in young companies, creates a rapidly evolving ecosystem of innovative industries. Cloud is an innovative IT concept for the IT infrastructure organization consisting of distributed and shared configured hardware and network resources, as well as software deployed at remote (cloud) vendor (provider) centers ). That is, the cloud is a new approach in the organization of IT infrastructure. Cloud computing is a model of providing ubiquitous and convenient on-demand network access to a pool of shared configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be quickly deployed and released with minimal effort to manage or interact with the provider (provider). This cloud model is represented (described) by five main features, three service models and four deployment models. [2].
Presentation of the main material and the justification of the results. "Cloud" means a complex infrastructure with many technical details hidden in "clouds". The NIST Definition of CloudComputing v15 defines “cloud computing” as follows: the cloud computing model provides convenient network access to a shared pool of computing resources that configurable (eg, networks, servers, storage, application, services); the cloud model promotes accessibility and is characterized by five basic elements (self-service on demand, wide network access, pooled resources, independent location, fast flexibility, measurable services).There are many cloud solution providers available today. Big companies like Amazon, Google, Microsoft, etc. offer significant discounts to educational institutions, giving them access to cloud services virtually free of charge.
Before every business, sooner or later the question arises which cloud to choose. There can be no single answer here. Because every business has its own peculiarities, advantages and specific risks. It is recommended to take into account at least two major factors: how much the desired IT services will address and the level of potential information security risks. Based on practical and theoretical research in the field of cloud technology, seen as a tool for business outsourcing, it is important to highlight the point where a significant proportion of large companies use public cloud services for end customers or for external ( remote) employees. And the core systems for full-time employees are concentrated in a private cloud. However, big business and most mid-level entrepreneurs prefer private or hybrid clouds (technology). This is due to a factor such as the availability of an advanced IT service, which makes it more profitable and easier to manage your private cloud than to move your entire computing infrastructure to the public domain.Given the current situation, in the presence of potential IT security problems, the attractiveness of cloud services is still actively growing, and today there is considerable interest from the business community in this trendy outsourcing trend.
Increasing the attractiveness of cloud products for Ukrainian businesses is directly dependent on the mass of the company's presence on the Internet's global network. Equally important factor in the active use of cloud services is the rapid development of IT outsourcing, which makes the business gain geometric optics as a result of the interference of the direct beam and the beam reflected from the earth's surface a number of benefits from using new development mechanisms. Speaking of cloud computing, one has to say about a possible evolution of IT that the market may reach in the future. Analysts call this model IT as a Service (ITaaS). The name implies that this model assumes the consumption of all IT resources, be it hardware or software or service. In practice, this means bringing all the facilities to specialized data centers, placing the necessary applications in them, and renting the equipment to access these resources. Rental equipment is also serviced by the service provider. So far, such organization of supplier-customer interaction is practically not widespread in the Ukrainian market. It should be noted that in addition to the aforementioned advantages of cloud models, outsourcing non-core business processes to outsourcing companies and reducing capital expenditures on IT by translating them into operating systems makes the company more attractive to financial institutions [3-4].
If the model (concept) of providing distributed and shared configured computing resources meets the above characteristics, then it is cloud computing. Cloud computing service models or cloud computing:
- software as a Service (SaaS) is software as a service. In this cloud computing model, the consumer uses vendor applications running on a cloud infrastructure that are accessible to the client via a web browser or application interface. Consumers cannot manage and control the underlying cloud infrastructure, including networks, servers, operating systems, data warehouses, or even modify the parameters of a specific application.
- platform as a Service (PaaS) is a platform as a servant. A cloud computing model in which a consumer gains access to the use of a software platform: operating systems, database systems, application software development and testing tools. In fact, the consumer leases a computer platform with the operating system installed and specialized development tools. The consumer does not manage the underlying cloud infrastructure, including networks, servers, operating systems, or data warehouses, but manages deployed applications and possibly configuration settings for the environment.
- infrastructure as a Service (IaaS) - infrastructure as a service. A cloud computing model in which the consumer is able to manage processing and storage, as well as other basic computing resources (virtual servers and network infrastructure), on which he can independently install operating systems and applications for his own purposes. Essentially, the consumer leases abstract computing power (server time, disk space, and network bandwidth) or uses IT infrastructure outsourcing services. The consumer does not manage the underlying cloud infrastructure, but manages operating systems, storage, and deployed applications [5].
Cloud computing deployment models, ie cloud computing:
- private cloud is an infrastructure designed to use cloud computing in the headquarters of one organization.
- community cloud is a cloud-based infrastructure that is designed to exclusively use cloud computing by a specific consumer community from organizations that solve common problems.
- public cloud is an infrastructure designed for the free use of cloud computing by the general public.
- hybrid cloud is a combination of various cloud infrastructures (private, public) that remain unique objects but are interconnected by standardized or private technologies that enable data and application sharing.
Current information technologies allow the management of companies to completely abandon the installation and use of special software, from their systematic updating. The essence of cloud technology is that Ukrainian businesses may not have any programs on their computer. Only one thing is fundamentally important: having a stable high-speed Internet. Everything you need is presented on the Internet. Therefore, cloud technology for domestic businesses is a kind of Internet-based service model, a list of hardware and software required to process and execute client applications from a growing business. The benefits of cloud technology as an IT outsourcing tool can hardly be overestimated. Clouds make it possible to take small and narrow-minded areas of business beyond the boundaries of business, enabling business directors to focus on core business processes without distracting themselves from secondary tasks [6].
Today, there are many attractive offers in the market for outsourcing services in the field of cloud technologies and at least 9 models, including: IaaS (renting of IT structure), BPaaS (services for solving business problems), SaaS (renting of applications), PaaS (application development), DaaS (virtual desktop), CCaaS (virtual convention center), SecaaS (information security for rent), BaaS (backup as a service), DRaaS (disaster solution). Based on these models, a business understanding of cloud service practices is formed, which essentially enables a business to abandon its own information infrastructure by offering services and assistance to a software-based platform or software from a specialized organization.
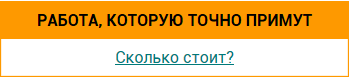
Leading global developers, including well-known scientists, are working hard to further develop service clouds. Given the current realities and trends of information technology development, the cloud is divided into three types: private (public cloud), public (public cloud) and hybrid (hybrid cloud) (Pic 1).
Pic 1 Types of "cloud" services
For some educational institutions it may be advantageous to move to the cloud of internal learning management systems (LMS). This is a good opportunity for those institutions that cannot afford to buy and maintain expensive hardware and software that can optimize IT infrastructure costs in today's environment.
Cloud programming. Modern programming practice involves the active use of specialized integrated development tools (IDE - Integrated Development Environment). Their use has two complexities:
- configuring and installing IDEs requires a high level of system administrator skills. This leads to the need to hire highly qualified staff to become a system administrator, whose salaries may be a significant cost item in the educational institution's budget;
- modern IDEs are quite demanding for the resources of the machine they are using. For example, one of the most common IDEs of Microsoft Visual Studio 2012 requires a processor with a power of 1.6 GHz or higher, 1 GB of RAM (or 1.5 GB for a virtual machine), 10 GB of free disk space. Most educational tasks do not require computers with such high performance, so buying them may be an unacceptable luxury [7].
Email was one of the first cloud services to be used by European educational institutions. E-mail service outsourcing is not a difficult task, which clearly does not play a key role in the work of an educational institution. Google and Microsoft provide employees and students with access to e-mail for free. In addition to email services, these corporations provide the ability to use the standard office suite in the cloud to collaborate with electronic documents, spreadsheets and create presentations. Cloud services for Google Apps for Education and Microsoft Office 365 for education allow you to use built-in messaging, shared scheduling calendars and shared address books. Each cloud user receives a large amount of disk space to store any information received as a result of the cloud operation. The free delivery of services to educational institutions is explained as follows. In today's cloud market, there is high competition between software vendors, so they try to provide their services to educational institutions for free. The calculation goes to future graduates who, after receiving their education, will get a job and will be able to persuade future employers to buy a software product that they already know about. If data security is not a priority for an educational institution, then it may be advantageous to use low-level IaaS Services as storage systems, such as video and audio [8].
The disadvantages of using cloud computing in terms of information security include:
- system complexity: A shared cloud is extremely complex compared to a traditional data center. The large number of components that make up the cloud allows you to attack at different levels of abstraction. In addition to components for general computing, such as application deployments, virtual machine monitors, guest virtual machines, storage, there are also components that include controls: selfservice, accounting resource, quota management, data replication and recovery, service level monitoring, management workload.
Common multi-user environment: The main drawback of public clouds is that they share resources and components with users who are not logically aware of them, allowing the attacker to exploit the mechanism of resource sharing among users and gain unauthorized access to resources by exploiting vulnerabilities inside the cloud. The uniformity of the software and hardware of the platform means that the only drawback will be visible throughout the cloud and potentially affect all users of services. Internet Usage: Cloud Services, as well as administering and managing cloud services and applications settings, uses an unsecured Internet network. As the organization moves to cloud computing, internal secure networks and resources have new information hazards that need to be addressed. There is also a need for remote administration using an unsecured data channel. Loss of control: When using cloud services, the user transfers control of the information to the cloud provider, which carries additional risks for information security. The user becomes dependent on the cloud provider and may lose not only logical control over the information, but also physical [9].
Conclusion and prospects for further research
Thus, the introduction of innovative technologies, in particular cloud, in various fields of educational activity (educational process, management and monitoring, research, exchange of pedagogical experience, etc.) can contribute to the modernization of education as a whole, its transition to a qualitatively new level, the development of principles of openness and humanism. Of course, the process of upgrading education cannot be limited to the use of cloud computing. Successful implementation of new technologies requires updating pedagogical approaches, methods and techniques, creative focus and personal motivation.
Further research we consider appropriate to focus on the creation of techniques for the use of cloud services in various fields of educational activity. Cloud computing is a combination of several key technologies that have been developed over the years and are considered by many researchers as the next generation of enterprise IT architecture. With all the benefits of cloud computing, there are many security issues that are not well understood today and are still under discussion.
As the article showed, the main problem that has not been resolved in the field of cloud computing today is user trust in the service provider. This problem is acute not only for companies and enterprises using third-party vendors, but also for ordinary users, whose personal data also need protection and security guarantees. If in the case of a large enterprise, it can protect itself against threats by conducting a security audit of a cloud service provider and analyzing risks and threats to information security, as well as insuring them or creating their own private cloud, then small companies or ordinary users do not have this opportunity. It is therefore necessary to implement controls for cloud service providers at the international or national level, with the aim of conducting a security audit and verifying their compliance with international or national standards and the conditions imposed on them. Future work plans to review and analyze existing cloud construction architectures in terms of their security.
References
1. Arkipov T.L., Zaitseva T.V. Cloud computing technologies in educational institutions // Cloud technologies in education. Proceedings of the All-Ukrainian Scientific and Methodological Internet Seminar (Krivoy Rog - Kyiv - Cherkasy - Kharkiv, December 21, 2012). Kryvyi Rih: KII Publishing Department, 2012. P.72.
2. Aleksanyan GA Use of cloud services Yandex in organizing independent activity of students of VET [Text] / GA. Aleksanyan // Pedagogy: Traditions and Innovations (II): International Materials. in absentia. scientific Conf. (Chelyabinsk, October 2012). Chelyabinsk: Two Komsomol members, 2o12. P. 150-153.
3. Cloud technologies in education: materials of the All-Ukrainian scientific-methodological Internet-seminar (Krivoy Rog - Kiev - Cherkasy - Kharkiv, December 21, 2012). Kryvyi Rih: KII Publishing Department, 2012. 173 p.
4. Koroleva A.S. On the possibility of using cloud technologies in education [Report]. Magadan: Municipal Autonomous Educational Institution “Gymnasium 24”, 2012.
5. Neil Sclater. Cloud computing in education: A case study. Moscow: UNESCO Institute for Information Technologies in Education, 2010.ISO/IEC 17788:2014(E). Information technology - Cloud computing - Overview and vocabulary: International Standard. Switzerland: ISO/IEC, 2014. 14 p.
6. The NIST Definition of Cloud Computing: Recommendations of the National Institute of Standards and Technology [Electronic resource]. Access mode: http://csrc.nist.gov/publications/nistpubs/800-145/SP800-145.pdf
7. Seydametova Z. S., Seytvelieva S. N. Cloud services in education // Information Technologies in Education. 2011, N9.
8. Sultanova N, Tishchenko D. Promotion of the use of information and communication technologies in technical and vocational education and training in the CIS countries [Report]. Moscow: UNESCO, 2012.
9. Voronkin O.S. Cloud Computing as a Basis for Forming Personal Educational Environments // Collection of Scientific Papers: Proceedings of the Second International Scientific and Practical Conference FOSS Lviv 2012, Lviv, April 2628, 2012 - Lviv, 2012. P. 143-146.
Размещено на Allbest.ru
...Подобные документы
Review of development of cloud computing. Service models of cloud computing. Deployment models of cloud computing. Technology of virtualization. Algorithm of "Cloudy". Safety and labor protection. Justification of the cost-effectiveness of the project.
дипломная работа [2,3 M], добавлен 13.05.2015Information security problems of modern computer companies networks. The levels of network security of the company. Methods of protection organization's computer network from unauthorized access from the Internet. Information Security in the Internet.
реферат [20,9 K], добавлен 19.12.2013Модели обслуживания облачных технологий (IaaS, PaaS, SaaS). Определение облачных технологий, их основные характеристики, достоинства и недостатки. Функции и возможности облачного решения Kaspersky Endpoint Security Cloud от "Лаборатории Касперского".
курсовая работа [626,7 K], добавлен 29.06.2017IS management standards development. The national peculiarities of the IS management standards. The most integrated existent IS management solution. General description of the ISS model. Application of semi-Markov processes in ISS state description.
дипломная работа [2,2 M], добавлен 28.10.2011Сrime of ciber is an activity done using computers and internet. History of cyber crime. Categories and types of cyber crime. Advantages of cyber security. The characteristic of safety tips to cyber crime. Application of cyber security in personal compute
презентация [203,5 K], добавлен 08.12.2014Основи проектування мобільного додатку для операційної системи Android з використанням хмарної бази даних Cloud Firestore. Аналіз основних труднощів, які виникають під час розробки додатків. Визначення основних переваг та недоліків хмарних баз даних.
статья [195,3 K], добавлен 07.02.2018Practical acquaintance with the capabilities and configuration of firewalls, their basic principles and types. Block specific IP-address. Files and Folders Integrity Protection firewalls. Development of information security of corporate policy system.
лабораторная работа [3,2 M], добавлен 09.04.2016Анализ существующих программ трехмерного моделирования. Сравнение программ для создания трехмерной графики. Технологии трехмерного моделирования в Cinema 4D. Проект создания текстовой анимации на основе инструментов "Organicball", "Formula" и "Cloud".
дипломная работа [2,4 M], добавлен 14.11.2017The material and technological basis of the information society are all sorts of systems based on computers and computer networks, information technology, telecommunication. The task of Ukraine in area of information and communication technologies.
реферат [29,5 K], добавлен 10.05.2011NANO Security - сплоченная команда молодых специалистов: программистов, аналитиков, тестировщиков, менеджеров. Предметная область, назначение разработки, требования к программному изделию, системы управления обучением. Обзор языков программирования.
отчет по практике [1,1 M], добавлен 22.07.2012Overview history of company and structure of organization. Characterization of complex tasks and necessity of automation. Database specifications and system security. The calculation of economic efficiency of the project. Safety measures during work.
дипломная работа [1009,6 K], добавлен 09.03.2015The need for Colvir's functional modules to avoid the costs of training and to facilitate modification and interaction of system components. Description and practical use of Citrix server and CyberPlat - integrated universal banking online payments.
доклад [505,3 K], добавлен 05.09.2011Математическая основа параллельных вычислений. Свойства Parallel Computing Toolbox. Разработка параллельных приложений в Matlab. Примеры программирования параллельных задач. Вычисление определенного интеграла. Последовательное и параллельное перемножение.
курсовая работа [1,1 M], добавлен 15.12.2010A database is a store where information is kept in an organized way. Data structures consist of pointers, strings, arrays, stacks, static and dynamic data structures. A list is a set of data items stored in some order. Methods of construction of a trees.
топик [19,0 K], добавлен 29.06.2009Сравнительная характеристика антивирусных программ. Фирма-разработчик и характеристика программы Eset Smart Security, форма продажи лицензий и структура модулей защиты информации. Назначение утилиты Eset SysInspector. Правила корректного обновления.
контрольная работа [28,8 K], добавлен 10.03.2011Web Forum - class of applications for communication site visitors. Planning of such database that to contain all information about an user is the name, last name, address, number of reports and their content, information about an user and his friends.
отчет по практике [1,4 M], добавлен 19.03.2014Классификация вирусов, методы защиты от них. Виды и типы антивирусных программ. Антивирус Kaspersky Internet Security 2012, компоненты защиты и мониторинг сети, достоинства. Динамика изменения возможностей антивирусов по лечению активного заражения.
курсовая работа [467,8 K], добавлен 06.09.2013Consideration of a systematic approach to the identification of the organization's processes for improving management efficiency. Approaches to the identification of business processes. Architecture of an Integrated Information Systems methodology.
реферат [195,5 K], добавлен 12.02.2016Data mining, developmental history of data mining and knowledge discovery. Technological elements and methods of data mining. Steps in knowledge discovery. Change and deviation detection. Related disciplines, information retrieval and text extraction.
доклад [25,3 K], добавлен 16.06.2012Technical and economic characteristics of medical institutions. Development of an automation project. Justification of the methods of calculating cost-effectiveness. General information about health and organization safety. Providing electrical safety.
дипломная работа [3,7 M], добавлен 14.05.2014